Hi There!👋🏻I am Guru HariHaraun.
DevSecOps & cybersecurity professional with a Master of ITS (Cybersecurity) from the University of Canberra, Certified Ethical Hacker and Junior Penetration Tester with 6+ years of applied research and lab building in red-team pentesting, secure SDLC, and threat detection—plus experience as a full-stack developer, cloud engineering enthusiast, and SEO strategist.
Experience
Graduate DevSecOps Developer
Fifth Domain
Braddon, Canberra, Australian Capital Territory
- Embedded OWASP-aligned controls directly into the CI/CD pipeline, mapping attack paths against MITRE ATT&CK and running SAST, DAST, code reviews, and focused penetration tests. The outcome was risk-driven remediation and tighter least-privilege designs.
- Hardened AWS and GCP estates by securing VPCs, subnets, gateways, Kubernetes clusters, and Docker environments. Enforced IAM segmentation, firewall rules, and both site-to-site and client VPNs, while keeping backup strategies aligned with defined RTO/RPO targets. Also tuned performance and high availability across multiple availability zones.
- Kept runbooks, CMDB entries, and KCS articles accurate and current, while resolving L2/L3 incidents through the Intercom service desk. Worked with vendors, oversaw UAT, and tracked SLAs to keep cyber-range labs reliable and responsive.
Key Takeaways:
Docker
Security Information and Event Management (SIEM)
Information Security
Amazon Web Services (AWS)
Ethical Hacking
Virtual Machines
Kali Linux
Cybersecurity
Technical Documentation
Technical Writing
Vulnerability Assessment
Cloud Computing
Google Cloud Platform (GCP)
Kubernetes
Terraform
Ansible
Linux
Git/GitLab CI
Python (Programming Language)
Amazon VPC
Content Quality Assurance Officer
Fifth Domain
Braddon, Canberra, Australian Capital Territory
- Led the Quality Assurance (QA) for Capture The Flag (CTF) and Vulnerable Lab challenges, ensuring alignment with NIST and MITRE ATT&CK frameworks, and enhancing course quality.
- Developed and deployed varied Virtual Machines (VMs) in cybersecurity-focused environments using AUCloud and AWS EC2, creating realistic cyber threat landscapes for comprehensive training scenarios.
Key Takeaways:
Docker
Amazon Web Services (AWS)
Security Information and Event Management (SIEM)
Team Leadership
DevSecOps
Virtual Machines
Technical Documentation
Microservices
Cyber Operations
Head Teacher
CodeCamp
Canberra, Australian Capital Territory
- Teaching coding fundamentals and programming concepts to more than 80+ primary school students in Canberra and providing directions to the teaching assistants to create a positive classroom environment.
Full Stack Developer & SEO Stagiest
Gopaldass Industrial Services
Tiruchirappalli, India
- Built a Digital Vehicle Log Management System (DVLMS) to handle the data of customers and attenders.
- Developed and Optimized a Web Portfolio for the company, Migrated and boosted the company’s online presence.
Key Takeaways:
Google My Business
Search Engine Optimization
Search Engine Marketing (SEM)
Amazon Web Services
UI/UX
PHP
MySQL
GIT
Docker
Cybersecurity Intern
Virtually Testing Foundation
Los Angeles, USA
• Main Objective
The key objective of this Internship is to leverage my skills and to gain real-world experience in designing the network architect and to Implement security for the networks.
Key Takeaways:
Virtualization Security
Kubernetes
Cloud Security
Network Security
Network Penetration
ESXi
vCenter
DRS
Virtual Machines
NSX
DRS
IDPS
URL Analysis
Virtual Storage Network(vSAN)
Distributed Firewall
Risk Informed Cyber Security
Security Analyst Virtual Intern
Australia And New Zealand Banking Group
Melbourne, Australia
• Social Engineering Investigation
Investigated the E-mails received/sent by the company and report the email witch has any suspicious items which may be harmful to the company.
• Digital Investigation
Analyzed a packet capture file using an open-source tool to identify and Investigate for any potential threats.
Key Takeaways:
Social Engineering Concepts
Security Report Writing
Analyzing Network Traffic
Identification of File Types
Digital/Open Source Investigation
WebMaster & Cloud/System Admin
Xplore Service: Crowdsourcing
New South Wales, Australia
- Xplore Services is a charity organization who are working behalf with UNICEF Australia & UNHCR.
- Developed a Fund-Raising platform to organize and maintain dynamic access for their public assets.
- Deployed the application on AWS Cloud using Nginx server and orchestrated. Also, worked on Search Engine Optimization (SEO) for their organization.
Key Takeaways:
HTML
CSS
NodeJS
MongoDB
Nginx
AWS
SLA
IAM
Load Balancer
Orchestration
Search Engine Optimization (SEO) Tools
Deployment
Version Control
LEADERSHIP
Chairman
SVCE Cyber Hub
A club dedicated especially to students interested in the field of information security and networking. I'm in charge of pushing the club's boundaries and organizing events, seminars, and workshops for students.
Creative Head
Association of Computer Engineers (ACE)
My main objective is to lead the Association of Computer Engineers (ACE) Design Team, and I had overall responsibilities for the outcome of any design endeavoured by designers at ACE.
Graphic Designer
Association of Computer Engineers (ACE)
As the Executive of the ACE Design Team, I was in charge of creating modern and imaginative artworks for the club. I was in charge of double-checking the designs and revisions made by peers.
Education
Masters of Information Technology and Systems in Cybersecurity
University of Canberra
Canberra, Australian Capital Territory
Course Works
- Professional Practice in IT
- Systems Analysis and Modelling
- Security and Support in IT
- Introduction to Information Technology
- Technological Innovation and Entrepreneurship
- Introduction to Cyber Safety
- Information Security Research Methodology
- Technology and Engineering Management
- System and Network Administration
- Cloud Computing Architecture
- Advanced Cyber Security
- Contemporary IT & E Issues
- Technology Capstone Research Project
- Information Security (PG)
- Introduction to Digital Forensics
Bachelors of Computer Science and Engg.
Sri Venkateswara College of Engineering, Anna University
Chennai, India
Course Works
- Computer Programming
- Programming and Data Structures
- Computer Architecture
- Internet Programming
- Operting Systems
- Database Management Systems
- Internet Programming
- Computer Networks
- User Interface Technologies
- Software Engineering
- Machine Learning
- Artificial Intelligence
- Cryptography and Network Security
- Mobile Computing
- Multi-Core Architectures &Programming
- Advance Software Engineering
Higher Secondary School
Campion Anglo-Indian Higher Secondary School
Tiruchirappalli, India
Stream: Physics, Chemistry, Math and Computer Science.
Certifications
eLearnSecurity Junior Penetration Tester (eJPT) is a 100% practical certification on penetration testing and information security essentials. Instead of answering through a series of multiple-choice questions, we are expected to perform an actual penetration test on a corporate network. This penetration test is modeled after a real-world scenario. eJPT is the only practical certification that proves to have essential Penetration Testing skills
Key Takeaways:
TCP/IP
IP Routing
LAN protocols and devices
Basic vulnerability assessment of networks
Essential penetration testing processes & methodologies
HTTP and web technologies
Basic vulnerability assessment of web applications
Exploitation with Metasploit
Simple web application manual exploitation
Basic information gathering and reconnaissance
Simple scanning and profiling the target
With this certification, I am cognizant of the modern network security, operating system hardening, firewalls, intrusion-detection systems, VPNs and Encryption, Physical Security, Standards, System Security and Security Policies in this certification.
The U.S. Department of Homeland Security with Cybersecurity and Infrastructure Security Agency (CISA) provided the 210W-06 ICS Cybersecurity Threats training. This training covered three attributes of human threat, differentiate between the three categories of threat actors, explained the risk curve as it relates to threat groups, describes intentional versus unintentional “insider” cyber threats, discussed threat trend for industrial controls systems and describe the attacker tools and techniques used by hackers and penetration testers.
certified Ethical Hacker (Practical) is a six-hour, rigorous exam that requires to demonstrate the application of ethical hacking techniques and to solve a security audit challenge within a given limited of time, just like in the real world. The exam was developed by a panel of experienced SMEs which includes 20 real-life scenarios with questions designed to validate essential skills required in the ethical hacking domains as outlined in the C|EH program. It is not a simulated exam but rather, it mimics a real-world corporate network through the use of live virtual machines, networks, and applications designed to test ethical hacking skills.
Key Takeaways:
Threat Vector Identification
Network Scanning
OS Detection
Vulnerability Analysis
System Hacking,
Web App Hacking.
Steganography
Steganalysis attacks
Malware Exploitation
Packet Sniffing
Web Server Attack
SQL injection attacks
Cryptography Attacks
Chaos Engineering is quickly becoming a career requirement for engineering teams focusing on reliability. Understanding the myriad Gremlin attacks and their use cases, how to use Gremlin and Chaos Engineering for more efficient postmortems, creating advanced Chaos Engineering Test Cases and Scenarios, and more were all covered in the Gremlin Chaos Engineering Practitioner exam.
Key Takeaways:
Gremlin Certified Chaos Engineering Practitioner
SRE
Chaos Engineering
Site Reliability Engineer
DevOps
Failure Injection
Reliability Engineering
Fortinet Network Security Expert Level 1: Certified Associate
Fortinet Network Security Expert Institute
The Fortinet Network Security Expert Level 1: Certified Associate course delves into the real-world cyber dangers that endanger consumers and businesses. The course also taught us how to take precautions to protect ourselves and others from harm. It also clarified fundamental phrases and concepts to aid you in your quest to have a better understanding of cybersecurity.
This certification helped me to have a broad understanding of the cloud computing architecture, some of the service management, data management, resources management in cloud computing. Also, It covered cloud security, cloud simulator and few open sources and commercial clouds available in the market. Introduced to the docker and usage of docker in today's world, research trend in cloud computing and fog computing.
As a sub-mission, I took this course consist of introductory knowledge of cyber-security, which includes the global implications of cyber threats, the impact of cyber-attacks on industries, and why cybersecurity is a growing profession. I understood how networks are vulnerable to attack and Cisco’s approach to threat detection and detection and defence. On completion of this course, I have insight into opportunities available for pursuing network security certifications.
As the custodian for STTP Programme (Dedicated 15 Days Cyber Security Training Program ) (#STTP0x01) instituted by #WeArePlymouths.I gain knowledge on the methodologies and techniques which are used by a cyber-security person in the real-time. I have got a privilege to be a part of this training program.
External Achievements
Hack The Box is an online platform that helps to test our penetration testing skills. It consists of Vulnerable machines where we need to apply our pen-testing skills to crack the box. At last, we need to submit the User and Root Flags to get points. With having HACKER Badge, I've owned 7+ Boxes with 33+ points. Also, solved 20+ CTF's on it. Hack The Box is a great platform to exchange ideas and methodologies with thousands of people in the Information Security field.
As a techie, I was expanding my knowledge by reading a variety of blogs and articles, but there was a notion that if we taught people what we had learned, we would gain knowledge twice as much. Writing in a medium (online publishing platform) isn't ideal for a developer, so I created my own online blog publishing platform application and began contributing there.
As a hobby, I started my YouTube channel 8 years back and posting some of my interests. But a few years after, my interests diverted towards Information security domain. I conceived myself to upload contents which I learn about cybersecurity then, I started to use it for documenting my works as the proof of concept(POC) which might help the cybersecurity aspirants to learn whatever I have done.
SKILL
Familiar Languages, Tools & Frameworks













CI / CD Devops Tools & Frameworks











VA / PT Tools & Frameworks















Design









Databases


Recent Work

Co-WIN Vaccine Notifier bot for India
CoWIN Vaccine Notifier is a python based alert bot that checks the CoWIN portal periodically and if the vaccination slot was available for the user details which you given, it may send the email alert or an SMS alert. The Application is driven through the Flask framework (it is a micro web framework). The frontend application was deployed and hosted on Heroku (PaaS).

Undetectable Backdoor Malware
Using python and created a malware which tends to stream data between the victim and hacker. Moreover, the hacker could even pwn(take over) the victim's machine shell. Sessions are created within the hacker's code, so that the machine could listen for multiple bind connection. Also, hosted the hacker's machine on EC2 Instances on Amazon Web Services (AWS).
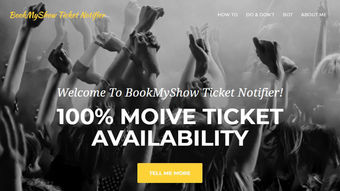
BookMyShow Ticket
Notifier
Getting tickets for the Avengers movie on the first day isn't easy. Using the Flask framework (it is a micro web framework used to deploy web applications in python) & beautiful Soup (a python literary used to scraps the data from the web pages) I've made an automated script which keeps on checking and notifies user when the ticket booking starts. Also, hosted on Heroku (PaaS).
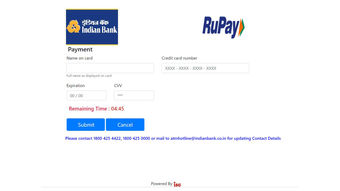
Payment Gateway Phishing Attack
In the modern world, shopping, movies, foods, Banking etc. Everything is done through the Internet. This is a cool thing but, on the flip-side, it has lot's of vulnerable threat too. Phishing is one of the social engineering attack done by hackers now days to get the credentials of the users. So I've recreated a XYZ Bank's payment gateway module and performed the attack in this project.
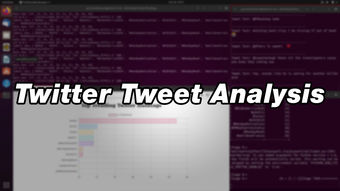
Twitter Tweet Analysis
Using Apache Spark (an online streaming Real-Time Analytics Platform) to process the tweets and identifying the trending hashtags from Twitter and, finally, retrieve top hashtags and representing the data in a real-time dashboard using the Flask Framework with sizzled up with some HTML5, CSS3 and Java script. The tweets are scrapped or recieved with Twitter developer's account.
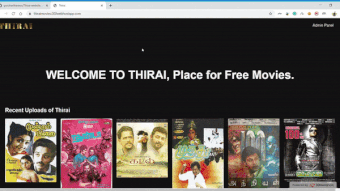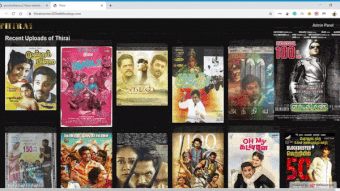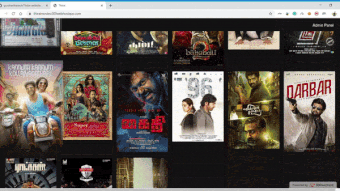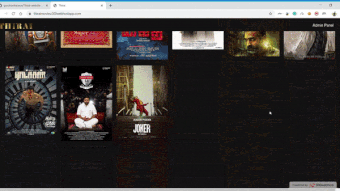
Online Movie Presenter for small organisations
Since in these modern days, the worth for watching movies on online has drastically grown. In this project, you can upload the Movie details like Movie Name, Movie Image, Director, Cast, Storyline and much more. Also, the cool features are, we can even upload the Movie file or torrent file to the webserver. All these details can be viewed by the users.
User Registration & Login systems in Node.js using MongoDB
Simple User Registration & Login systems app done with Node.js Framework using MongoDB(Atlas) as the data store, Express as the routing system, Body-parser as the parser for web page, Express-session used to track the user's session and of course Mongoose to make interacting with Mongo DB from Node app.
Contact me
Alternatively, You Can Download My PGP Key Here
